Xede: Practical Exploit Early Detection [1]
作者:Meining Nie (Institute of Software, CAS)
As all walks of life rely heavily on IT systems, Advanced Persistent Threat (APT) has become one of the most serious information security issues, posting a great threat on the government departments, research institutions, military organizations and industry enterprises. APT often employs zero-day (or recently-disclosed) vulnerabilities in popular programs, such as Microsoft Office [2], to penetrate the defenses of its target, and usually combines code reuse and code injection techniques to bypass exploit-mitigation mechanisms deployed in modern operating systems.
Traditional signature-based malware detection systems have increasingly become ineffective against APT. Instead, an effective defense mechanism should focus on the early detection of exploits. Exploits often violate some code or control-flow integrity. For example, code injection attacks introduce new (malicious) code into the system, while code reuse attacks manipulate the control flow to execute its gadgets. An exploit detection system checking these integrities could detect a wide spectrum of exploits.
However, the practical exploit detection is still a challenging problem in several ways, including:
- Almost all thepopular applicationsgenerate dynamic code to improve performance or extend the functionality. For example, as shown in table 1, to load a normal doc file, word.exe may generate about 76 KB codes which are very similar to the alien codes injected by the attacker. That may cause high false positives.
- Manyapplications replace or adjust the return addresses on the stack for obscure reasons. These irregular behaviors disrupt security mechanisms expecting the call and ret instructions to be matched. Table 1 shows that opening a normal pdf file could lead to about 85,000 false positives.
- Benign windows applications have many short code sequences that resemble gadgetsused in code reuse attacks, and are wrongfully detected as such by existing schemes [3]. For instance, as shown in table 1, we observe around 5,000 false positives when simple existing detection schemes are employed to analyze one PDF file.
- Many exploitdetectors launch samples in a sandboxto analyze their runtime behaviors. But exploits are always tied to specific run-time environments. If the exploits fail to compromise the system, they also fail to conduct malicious behaviors, so that they may bypass the detection. Our experiments reveal that around 70% of the malware samples are unstable. Table 1 shows that the success rate of pdf exploits in our dataset is less than 10%.
| Sample type | Size of benign DGC | Number of benign mismatched call-ret | Number of benign gadgets | Exploit success rate |
| doc | 78,216 | 4,561 | 4,221 | 74.14% |
| 24,308 | 84,798 | 4,997 | 9.52% |
Table 1. Possible false-positives in doc and pdf
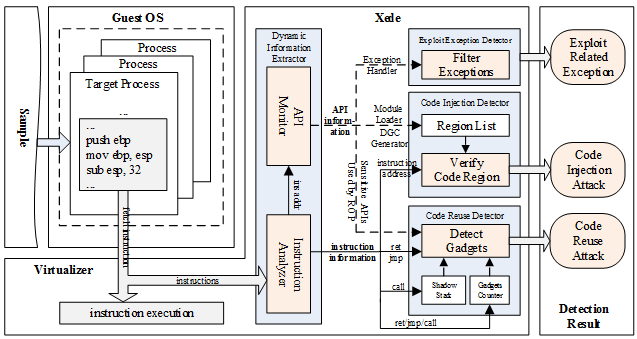
Facing the problems above, by analyzing the control flow transfers caused by exploits, we present a practical exploit early detection system called Xede, to comprehensively detect code reuse and code injection attacks. Figure 1 shows the architecture of Xede. It has three major detection engines:
Figure 1. The Architecture of Xede
- Exploit exception detectoranalyzes the program exceptions to discover the attack attemptswhich fail to compromise the systems. We intercept the page fault handler to detect the memory access violations caused by exploits. We also analyze the handling process of page faults to filter out those caused by paging mechanism or lazy-allocation algorithm to eliminate false positives.
- Code injection detectordetects (malicious) injected code by comparing the addresses of executed instructions against a list of benign code regions.We hook a kernel routine to intercept the executable module loading events. Then we parse the PE structure of the module which is being loaded to locate the address and size of its benign code regions (that is, its executable-sections). To reduce false positives, we also hook the APIs about page allocation, page protection modification and heap allocation, so that this list of benign code regions can be timely updated with the legitimate dynamically generated code (DGC) as well.
- Code injection attacks are often combined with code reuse attacks to bypass the DEP protection.Code reuse detectorfocuses on the detection of code reuse techniques. For ROP detection, we maintain a shadow stack for return addresses to discover the mismatched call–ret instructions, like ROPdefender [4] does. For JOP detection, we measure the length of consecutively executed instruction sequences to discover the gadget-chains, like kBouncer [5] does. But we have improved the shadow stack in many ways, including the judgement strategy, the matching algorithm and the search pattern. We have also improved the gadget counting method. So that we can accommodate all the previously-mentioned exploit-like code patterns which widely exist in today’s benign programs.
We build a prototype of Xede and download 12501 exploits from some public databases to evaluate its effectiveness. Table 2 shows that Xede accurately detects all of these exploits. In particular, among these exploits, 51.47% exploits adopt the ROP techniques.
| Exploit techniques | Sample proportion |
| code injection | 75% |
| ret-based gadgets | 51.47% |
| jmp-based gadgets | 19.85% |
| exploit exception | 25% |
Table 2. Exploit sample proportion with different exploitation techniques
We also integrate Xede into the mail server of a university in China to detect exploits in emails, and deploy Xede on the Internet as a public service [6] to scan user-provided files. Xede detects 136 exploits out of 11,385 collected samples. Among which only 44.12% of exploits successfully succeed, which means that real-world exploits heavily rely on special system environments. We use some commercial anti-virus software to conform that many exploits can easily evade the detection of signature matching nowadays. As shown in table 3, Kaspersky achieves the lowest false negative that is still higher than 15%.
| AV software | Version | Date of DB update | False negative |
| Kaspersky | 15.0.2.361 | 24/05/2015 | 21 |
| McAfee | 18.0.204 | 24/05/2015 | 49 |
| Avira | 15.0.10.434 | 24/05/2015 | 22 |
| Norton | 22.2.0.31 | 24/05/2015 | 32 |
Table 3. False negatives of commercial anti-virus software
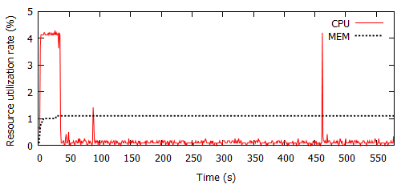
We evaluate the overheads of Xede in an Ubuntu 12.04 server with 3.07GHz Intel Xeon X5675 CPU and 32GB memory. Figure 2 illustrates that the rate of memory consumption and CPU usage are only 1.1% and 0.12%, respectively.
Figure 2. Resource consumption of Xede
Our evaluation demonstrates that Xede is highly effective and practical in detecting exploits.
参考文献:
[1].Meining Nie, Purui Su, et al. Xede: Practical Exploit Early Detection. RAID,
[2].Secunia: Secunia vulnerability review 2015. Tech. rep., Secunia (2014), http://secunia.com/vulnerability-review/.
[3].Schuster, Felix, et al. Evaluating the effectiveness of current anti-ROP defenses.RAID,
[4].Davi, Lucas, et al. ROPdefender: A detection tool to defend against return-oriented programming attacks. ACM, 2011.
[5].Pappas, Vasilis, et al. Transparent ROP exploit mitigation using indirect branch tracing. USENIX Security,
[6].TCA Malware Analysis platform.
[7].This research has been presented at the 18th International Symposium on Research in Attacks, Intrusions and Defenses(RAID 2015), published by Springer International, can be downloaded at http://link.springer.com/chapter/10.1007/978-3-319-26362-5_10.
[8].原文PDF下载:Xede: Practical Exploit Early Detection
作者简介:
Meining Nie is a Research Assistant in the Institute of Software, Chinese Academy of Sciences (ISCAS). His research focuses on systems security and malware analysis. He earned his Ph.D. in Computer Science from ISCAS (2016) in the area of malware analysis based on virtualization technology, studying under Prof. Purui Su. He received his B.E. degree in Computer Science from University of Electronic Science and Technology of China in 2010, and won the Second Prize of National College Student Information Security Contest in 2008.